This is an old revision of the document!
Table of Contents
Securing your devices
Key points:
Use a privacy screen / shield on your devices
If you use your computer, phone, or tablet in a public place — such as on a train, or in a café — buy a privacy screen for it.
A privacy screen is a sheet of plastic you place over your screen, which cuts down the viewing angle, meaning that people sitting next to you will find it harder to read your screen.
They are not perfect since, obviously, you still want to be able to see your screen when it is on.
You will get better protection against people sitting next to you than people sitting behind you, so you still need to think about how you are positioned.
Privacy screens are common for computers, and are increasingly common for phones, where they double as screen protectors.
For computers, I like the 3M “Gold” privacy screens.
Most computer privacy screens come with sticky tabs, so you can drop them into place easily.
Replace sensitive identifiers with pseudonyms
If you are reviewing a sensitive document, do you need to have the party names in it? If not, replace them with pseudonyms, so that someone who manages to see your screen gets less valuable information.
(This applies to physical documents too, if you're of the “print it out to review it” persuasion.)
Don't charge from public USB ports
The USB protocol carries both data and power so, when you plug your phone into a public USB port (e.g. at a café, train, or airport charging station), a malicious actor might be trying to connect to your device, as well as recharge it.
Use your own plug or battery pack
The safest thing to do is to charge only using your own plug / battery pack.
Use a USB data blocker
As an alternative, you can buy a USB data blocker — which some call as “USB condom” — which you connect between your device and the public USB port. These have the data lines cut, but still allow power to pass through.
Ideally, unlike the one in the photo here, your data blocker would be transparent, or easy to take apart, so you can verify that the data lines are cut.
Device-based protection
Recent versions of the iOS software require you to put in your passcode before “trusting” a device to send information to, or read information from, your phone or tablet.
Cover your webcam when you are not using it
There's a strong chance that, right in front of your face, there is a camera. And there's an equally strong chance that it is unobscured the whole time.
Stick something in front of the camera when you are not using it.
You can buy very cheap plastic slider webcam covers, or even cheaper multi-use stickers. Depending on your laptop, you might find that stickers are a better bet as, being thinner, they are less likely to interfere with your laptop closing or staying shut.
At a pinch, there's always a sticky note.
Do not cover the "camera on" LED
Whatever you use, if you have an LED near the camera, which turns on when the camera is enabled (or, at least, should turn on when the camera is enabled), make sure that your sticker does not cover it, so you can see if the LED is on or not.
Disconnect your microphone or at least try to get a notification when it turns on
While it's easy to do something about a camera, it's much trickier to do something about a microphone. And, realistically, the potential of someone listening to what you are saying is a greater risk to security than being able to take a photo of you.
Hardware-based approaches
If you do not use the microphone at all, you could open your laptop and physically remove or disconnect it. Alternatively, you could see if plugging a jack plug which does not connect to anything into your computer's microphone port fools your computer into thinking that an external microphone is connected, disabling your internal microphone. However, as this type of disabling is normally done with software, someone within control over your computer might be able to work around this.
Software-based approaches
If you are not able to remove or disconnect your microphone, consider software which attempts to detect if your microphone is switched on and warn you.
For example, for macOS, Micro Snitch.
Only install software / apps from trusted sources
Part of cybersecurity is protecting yourself from external attackers. Another part is protecting yourself from software running on your own devices, passing your data to a third party.
Although it is not a guarantee that your apps or software are not doing something malicious, getting them from trusted vendors which offer a meaningful review can reduce your risk.
For example, for macOS or iOS, this is Apple's App Store.
Check app permissions
When you install software, it may request your permission to access certain data or functionality of your device. For example, it might ask to access your address book, or to use your location.
Think about what the software is supposed to be doing for you, and consider (as best you can) whether those permissions are necessary.
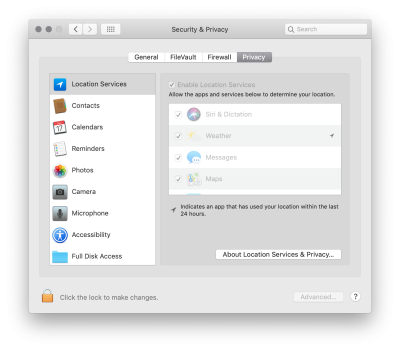
On macOS, you can see what software has requested which permissions, and what you have granted, in System Preferences / Security & Privacy / Privacy:
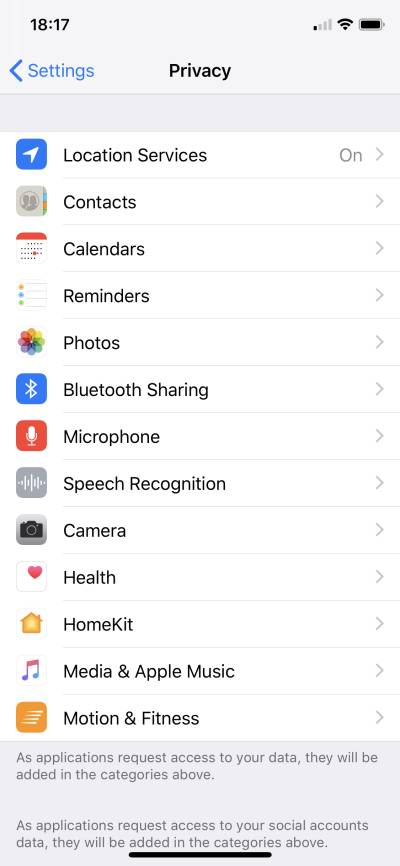
On iOS, it is Settings / Privacy:
Enable remote wipe functionality
If the facility is available to you, set it up. Learn how to use it. Ideally, set up a test device and run through the process of wiping it. Write down what you did, and keep copies of that somewhere accessible.
Routinely check it is up to date.
Probably have a monthly compliance checklist, of things you do each month to check your firm is running in a healthy manner: add this to the list.
You’re hoping that you’ll never have to use it, of course, but the last thing you want to be doing is panicking about how you do that remote wipe thing if you lose a device: follow a tested procedure, with which you are familiar.
Install software updates promptly
Balance between security and usability
Software updates may break software functionality: for example, I use a Mac, and use GPG for email encryption. I’m conscious that, because of the way GPGTools works, updates to the macOS mail client can break it.
So I tend to wait and see what other users experience when Apple releases a new software update before applying it to my machine.
Keep a log of your key software, and alternative options
Worth keeping a log of what software you rely on, and identifying an alternative so that, if your chosen software suddenly became unavailable, you know where to go. It may not be perfect — it may not need to be — but it might just keep you working rather than panicking.
May make you shy away from file types which can only be opened in one particular piece of software — something which you can open with a different, replacement piece of software gives you greater control and flexibility.